I graduated from The University of Abertay with a degree in Ethical Hacking in 2023. Now I work as a Cyber Security Risk Consultant. In this blog post, I want to share with you some of the differences between IT and OT Cyber Security that I’ve learned over the past few weeks. I find this topic to be rather interesting. Therefore I plan to make this into a series of blog posts, the next of which hasn’t been published yet.
Introduction
IT Cyber Security
IT security professionals are responsible for managing the data and information used to support business operations, and must be kept secure. OT professionals, on the other hand, is responsible for managing control of physical devices which equally must be kept secure.
IT security, is the practice of protecting, networks, computers, servers and and other information devices by implementing a security architecture with the goal of confidentiality, integrity and availability of data (CIA triad). IT security covers a wide range of domains, such as network security, application security, endpoint security, cloud security, and so on. In Ethical Hacking we learn how to breach the security of devices by learning to ask the right questions about how something works. Though the course I did covers stack-based buffer overflows and Perl scripting, there’s no mention of OT security at all. If Abertay were to add any module to the course I would hope it would cover OT Cyber Security through the guise of defence in depth.
IT security covers a wide range of domains, such as network security, application security, endpoint security, cloud security, and so on. In Ethical Hacking we learn how to breach the security of devices by learning to ask the right questions about how something works. Though the course I did covers stack-based buffer overflows and Perl scripting, there is no mention of OT security. If they were to add any module to the course I hope it would cover OT security through the guise of defence in depth.
OT Cyber Security
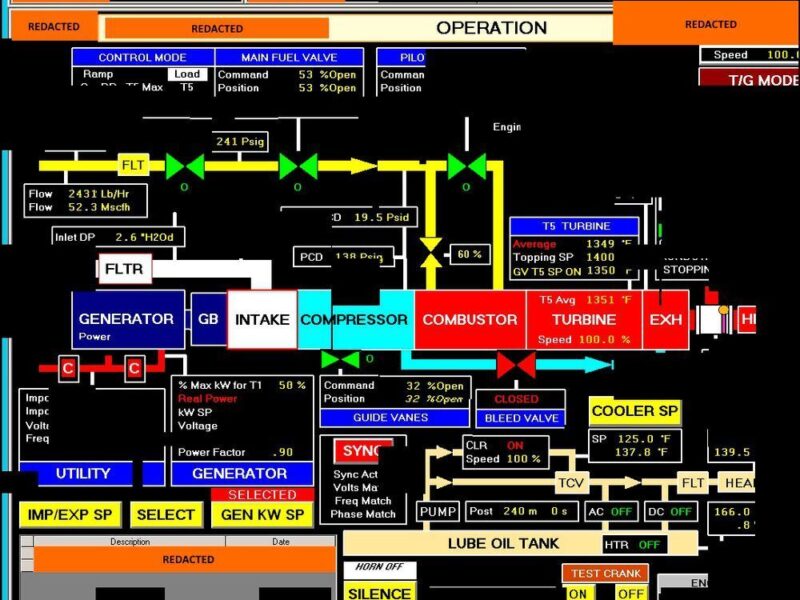
Operational technology (OT) security, is the practice of protecting OT systems which use purpose-built software and hardware for the monitoring and control of industrial systems. Typical OT systems include; industrial control systems (ICS), Industrial Automation Control Systems (IACS), supervisory control and data acquisition (SCADA) systems, distributed control systems (DCS). Typically hardware components in an OT system include; Remote Terminal Units (RTU), Programmable Logic Controllers (PLC). PLCs are usually connected to field devices such as sensors at one end and Human Machine Interfaces (HMI) at the other.
PERA Model
The OT technology components are broken down into layers in the PERA (Purdue Enterprise Reference Architecture). The model shows how Level 0 field devices connect to PLC, at Level 1 and upwards to terminal units, HMIs, SCADA and other servers. A breach in such systems could compromise the safety, reliability, and efficiency of industrial processes which more importantly could be part of critical infrastructure. OT security covers sectors such as energy, water, transportation, manufacturing, water, waste, and healthcare. Note that OT can be found anywhere there is an industrial process.
OT security feels like the other side of the coin from IT security. Imagine your personal laptop, it is in your care most of the time. The most likely form of malware comes from something you download. Should it get infected with ransomware there’s no real need for recovery of your device ASAP. Sure it’s inconvenient, but honestly, no one will be harmed and at most, you’re out a few hours. Get malware, just reinstall your OS, easy! In OT security things are a bit different, the consequences can cost billions and more importantly, can cost lives.
Different consequences
For OT security the goal is to assist a business with achieving its business objectives by ensuring the availability of systems while keeping the risk to people at a minimum. Imagine for a moment an FPSO gets pwned, flying someone out there in a helicopter to fix it is expensive and dangerous (the most dangerous part of the offshore process). Imagine the level of damage an attacker could do with control over a FPSO. A sufficiently advanced attacker could spill oil or worse cause a Piper Alpha type scenario. There’s no quick solution to an attack here, you can’t replace all the control systems. Operators can pull the plug but that will stop production which DOES cost, in some cases, millions per hour. OT security professionals have to implement solutions and protections to make breaches a near-impossible scenario.
Differences
As you can see, IT cyber security and OT cyber security have different goals, scopes, environments, and challenges. Here are some of the key differences that I’ve noted:
IT security focuses on confidentiality, integrity, and availability (CIA triad) of data and systems, in that order. Whereas OT security focuses on availability, integrity, and confidentiality (AIC) of physical processes and assets. This means that IT security prioritizes preventing data breaches and leaks. Where as OT security prioritizes preventing disruptions and damages to industrial operations. A surprising amount of the data in OT systems isn’t sensitive. Take the example of an FPSO again, there isn’t much data that needs to be confidential there. How much oil it produces is essentially public information as they have to report it. A lot of the metrics in Oil and Gas are inconsequential.
Environments
IT security operates in a dynamic and heterogeneous environment, where changes are frequent and divers. Think of how many unique devices connect to Starbucks’ AP every day. IT systems (typically, by best practice) are constantly updated, patched, replaced, or retired to keep up with the evolving threats and technologies. Generally, devices see about 5-7 years of use. IT security professionals need to adapt to these changes and ensure that the security posture is maintained or improved. On the other hand, OT security operates in comparatively a much more static and homogeneous environment, where changes are rare and costly. OT systems are often legacy, proprietary, or customized systems that have long lifespans and low interoperability. OT security professionals need to preserve the stability and functionality of these systems while addressing emerging threats and vulnerabilities. Remember in OT the priority is protecting the process from a safety and production view, not confidentiality. OT systems can see uses up to half a century. Think of Nuclear power plants, Oil rigs, EKG machines, and production logging servers.
Risk Based Approach

Both IT and OT security use a risk-based approach, where risks are assessed based on the likelihood and impact of a threat scenario. IT security professionals use various frameworks and methodologies to quantify and prioritize risks then implement appropriate controls to reduce them to an acceptable level. OT security professionals use various standards and regulations to define and comply with the minimum requirements for ensuring the safety and resilience of critical infrastructure. Some regulations have fines in the millions, but nothing can compare with the cost of an incident. The cost of the Deep Water Horizon oil spill has cost BP in excess of 70 billion USD to date. Whilst that was not a cyber incident, a similar incident could be caused through a cyber attack, scary stuff. Most importantly, nothing can compare with the cost of human life itself, which is always at risk in hazardous industries such as oil and gas.
Finding resources on IT security is very easy. Almost every resource for IT security covers TCP/IP but, there are very few that cover MODBUS. The hacktricks page only covers scanning with NMap. IT security professionals don’t have any trouble looking up information where as in OT security it can be hard to find information. This is due to the prevalence of vendor locked hardware, proprietary protocols and legacy systems.
Personal Challenges
One of the challenges that I faced when transitioning from IT security to OT security was how to understand cyber risk in OT environments. Unlike IT environments where risks can be measured in terms of data loss or financial impact, OT environments require a different perspective. One that considers the physical impact of attacks on human safety, potential environmental impacts and financial impact.
OT environments use wildly different technologies. I often find myself asking, what’s a PLC? What’s a BC-PLC8500-ACON? Even what’s a Zone?. To address this challenge, I’ve just been asking a bunch of questions, trying to wrap my head around things. Luckily my manager is very patient and is happy to take the time to help me understand the technologies, impacts and risks. We get into long conversations every now and again discussing systems, how they work and what the impacts could be. If you enjoy the theoretical OT cyber security risk is a great place to be.
Conclusion
The key here is that even though almost everything is different, the way we think critically about things is fundamentally the same. We still talk about AD creds, webservers and confidentiality. Just a lot less than other circles and with different priorities. The numbers behind everything here can be a bit daunting, as a professional just focus on doing a good job.
If you liked this post check out my post on the TryHackMe room Breaching Active Directory.