Enumerating Active Directory is a TryHackMe room that covers the various Active Directory enumeration techniques such as through CMD, PowerShell and Bloodhound. AD Enumeration can be a difficult undertaking especially if you don’t know what your looking for. Being able to enumerate over AD requires a relatively deep understanding of the structure of the domain which then can be used to determine attack paths that can then be used for lateral movement and ideally privilege escalation. This is the second walkthrough that I’ve written and directly follows the Breaching Active Directory room.
Task 1 – Why Active Directory Enumeration
Task one is an introduction, mostly consisting of preliminary knowledge, theory and setup. TryHackMe has the wonderful format of doing the boring stuff first so that you lose all motivation then begin the awesome stuff to pick you back up again. The information in this task will get you set up for the tasks ahead.
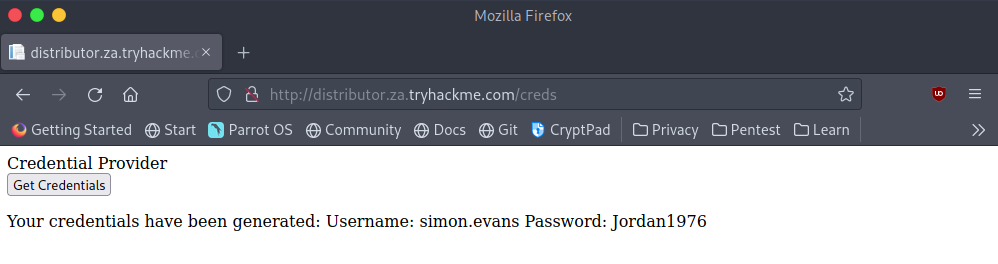
Head on over to http://distributor.za.tryhackme.com/creds from your connected VM to get the credentials we’ll use through out this room. You should see the same as below.
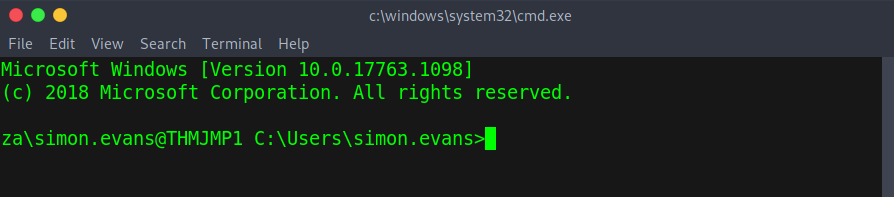
Now that we’ve got some credentials we are going to need to test them out. SSH into the “THMJMP1” machine. I’ll be using the command “ssh za.tryhackme.com\\simon.evans@thmjmp1.za.tryhackme.com” which results in:
Once everything is working mark the question on the task as done.
Task 2 – Credential Injection
Run as
To start with we are going to learn a bit about the “runas” tool. “runas.exe” is a command-line tool that enables one to run a command in the context of another user, it can be directly compared in principle to the Linux command “sudo”. Both tools make it possible to run a command pseudo as the specified user. You can read more about the “runas” tool on Microsoft’s official documentation.
DNS Problems
If you are using your own Windows machines for this room you’ll need to know how to configure an IP as your DNS server via the command line. Determining what IP on a network corresponds to a DNS server can be done in many ways which are detailed in this HackTricks page. However, to make things easier THM have told us that the DNS server is the domain controller on this network. If you’re on a Windows machine execure the following command:
$index = Get-NetAdapter -Name 'Ethernet' | Select-Object -ExpandProperty 'ifIndex'
Set-DnsClientServerAddress -InterfaceIndex $index -ServerAddresses <DC IP>You can test that everything is working using the command “nslookup za.tryhackme.com” If your DNS is not working try redoing the connection stage and resetting the network settings on your machine. Now we can finally test our our credentials. From the machine that you logged into earlier try listing the files in the domain controllers SYSVOL directory. The room doesn’t go through what this directory is used for and that information can be found nicely presented by Microsoft here.
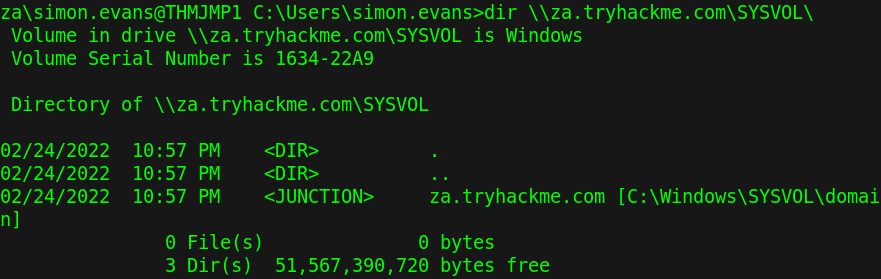
Read through the rest of the information provided and move onto the questions. Click on the question below to see the answer. However, it’s best you are able to figure it out yourself.
What native Windows binary allows us to inject credentials legitimately into memory?
runas.exeWhat parameter option of the runas binary will ensure that the injected credentials are used for all network connections?
/netonlyWhat network folder on a domain controller is accessible by any authenticated AD account and stores GPO information?
SYSVOLWhen performing dir //za.tryhackme.com/SYSVOL, what type of authentication is performed by default?
Kerberos AuthenticationTask 3 – Enumeration through Microsoft Management Console
The Microsoft Management Console (MMC) is the only GUI method of enumeration that we’ll use until the last task. Connect to the “THMJMP1” via RDP with the credentials we got in the first task. I’d recommend doing this over setting it up yourself as MMC in my experience can be temperamental. Once you’ve read through the tutorials this task should be very easy as it’s just opening the drop down menu on the left of the AD users and computers screen and finding an account. We can now move onto the questions.
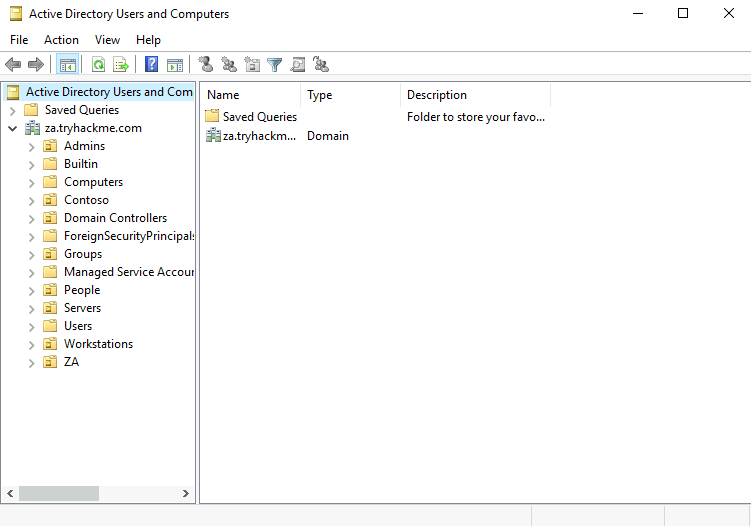
How many Computer objects are part of the Servers OU?
2How many Computer objects are part of the Workstations OU?
1How many departments (Organisational Units) does this organisation consist of?
7How many Admin tiers does this organisation have?
3What is the value of the flag stored in the description attribute of the t0_tinus.green account?
THM{Enumerating.Via.MMC}Task 4 – Enumeration through Command Prompt
Enumerating through command prompt should be the first option you go for when you have it available. Enumeration is all about sorting and managing information, I find that a command line utility provides me a way to filter information more efficiently. Read through the information provided and then we’ll move onto the tasks.
Users
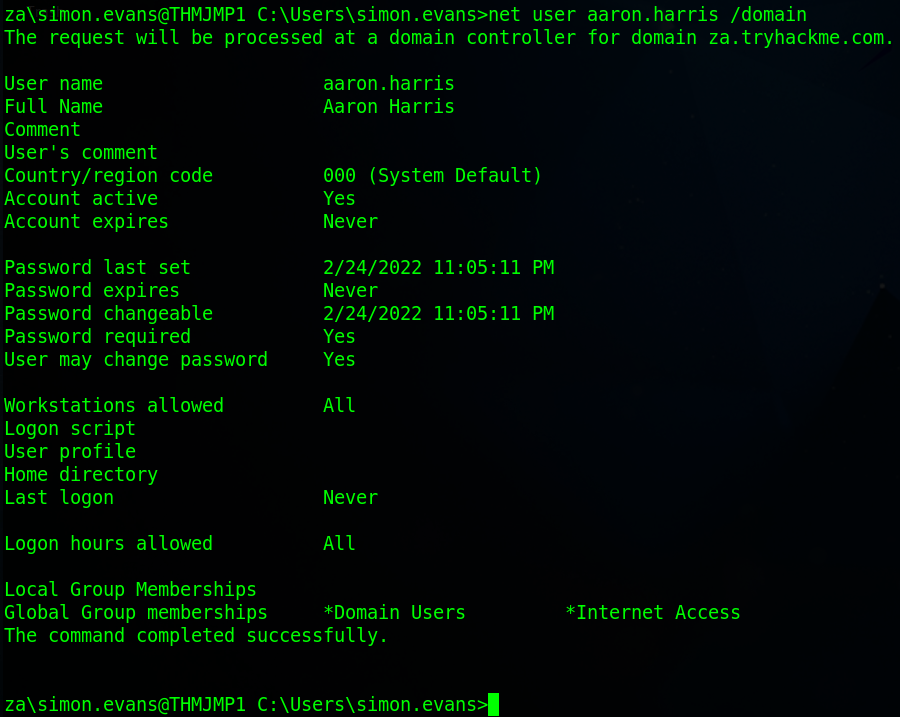
Enumerating over users can be very useful especially in CTF style tasks where password change dates or comments will be useful. To get stated the first question is to find out what other group arron.harris is a member of. To do this we’ll use the “net user” command from earlier with the “/domain” option after the username.
The next task is to find out if the Guest account is active. To do this we’ll list all users on the domain and pipe that to the “findstr” command where we’ll look for guest user. If there’s output that means that the account is enabled, if there is no output the account must be disabled.
Groups
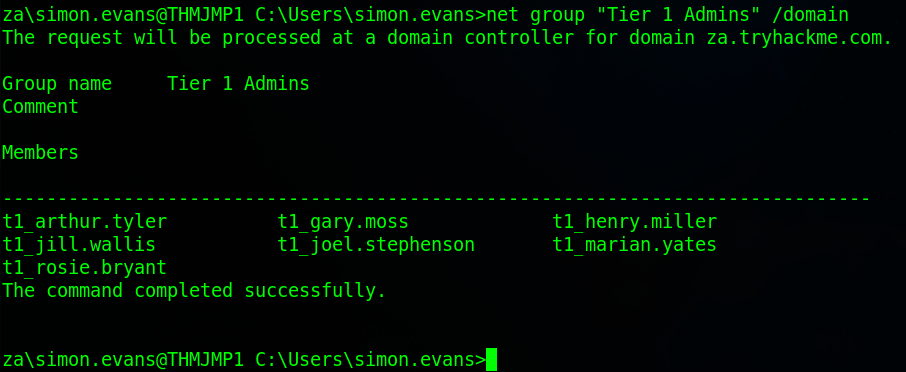
Firstly we need to fine out how many accounts are a member of the Tier 1 Admin group. To do this we’ll use the “net group” command with the “/domain” option after the group name. This command is very similar in syntax to the command we used earlier for the first question.
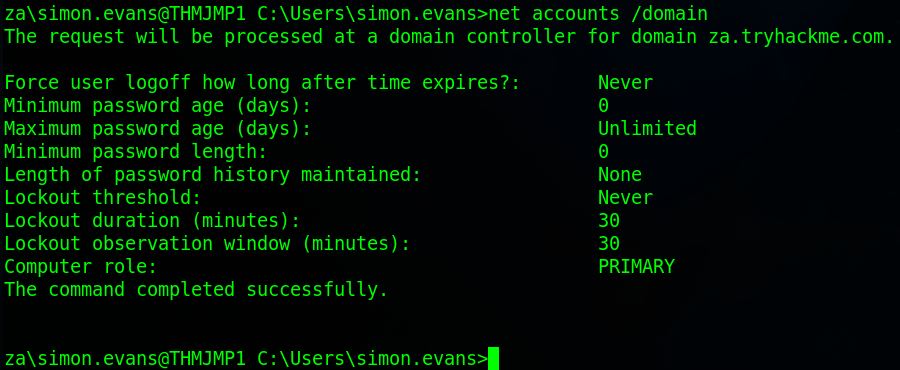
The final question wants us to determine what the account lockout duration of the current password policy is in minutes. Knowing when passwords are set to expire can be incredibly useful such as if the password expires every four months a common method of choosing passwords may be “Spring2022”. To find the password expiry date we’ll use the “net accounts” command with the “/domain” option.
Now we can answer the questions.
Apart from the Domain Users group, what other group is the aaron.harris account a member of?
Internet AccessIs the Guest account active? (Yay,Nay)
NayHow many accounts are a member of the Tier 1 Admins group?
7What is the account lockout duration of the current password policy in minutes?
30Task 5 – Enumeration through PowerShell
PowerShell is essentially a more extensive command prompt, much like the step up from sh to bash. You can upgrade your command prompt to a PowerShell using the command “powershell”. Firstly read through the information provided then we’ll move onto the task.
Tasks
Firstly we need to find the value of the title attribute of Beth Nolans account. Their username is “beth.nolan” and we’ll be using the “Get-ADUser” command where we’ll need to specify the user, server and that we want to see all properties. We’ll then filter that output using the “findstr” command to filter out for the Title attribute.
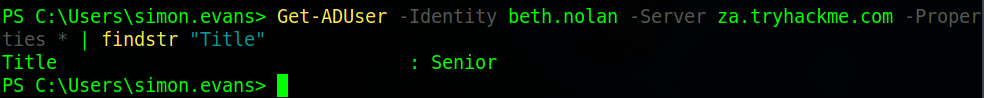
The next task is to find the value of the “DistunguishedName” attribute. we;ll use the same command as before this time filtering for “Dist” just to find the relevant information.
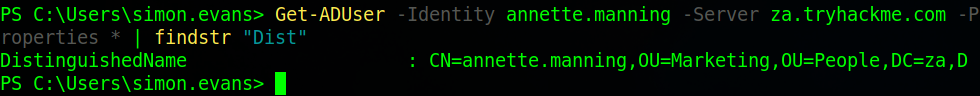
Now we are going to start looking at groups. To start with we need to find out when the Tier 2 Admins group was created. To do this we’ll use the “Get-ADGroup” command specifying the group, server and asking for all properties then filtering for “when” in order to find the “whenCreated” tag.
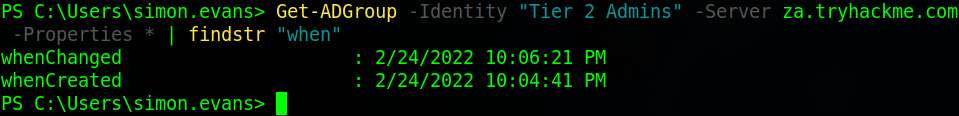
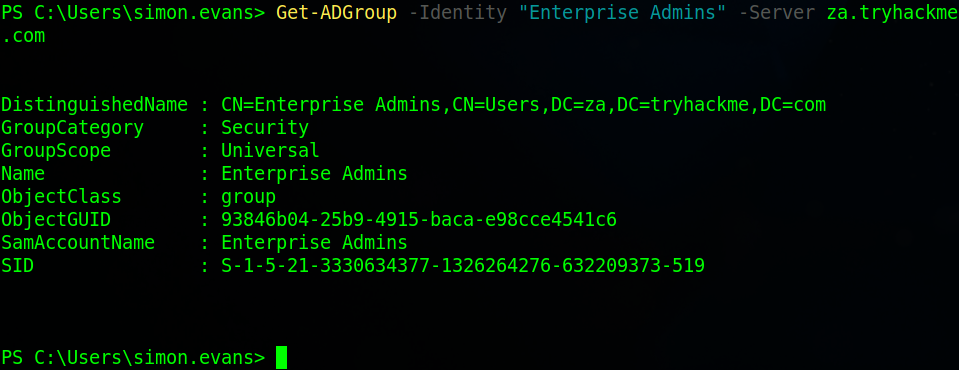
The next task is to find out the value of the SID attribute of the Enterprise Admins. Here I just used the “Get-ADGroup” command and looked at the output to get the SID value.
The last task is to find what container is used to store deleted AD objects. To do this we’ll use the “Get-ADDomain” command and filter for the string “Deleted”
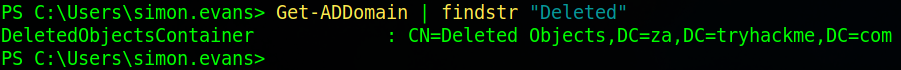
Now we can answer the questions.
What is the value of the Title attribute of Beth Nolan (beth.nolan)?
SeniorWhat is the value of the DistinguishedName attribute of Annette Manning (annette.manning)?
CN=annette.manning,OU=Marketing,OU=People,DC=za,DC=tryhackme,DC=comWhen was the Tier 2 Admins group created?
2/24/2022 10:04:41 PMWhat is the value of the SID attribute of the Enterprise Admins group?
S-1-5-21-3330634377-1326264276-632209373-519Which container is used to store deleted AD objects?
CN=Deleted Objects,DC=za,DC=tryhackme,DC=comTask 6 – Enumeration through Bloodhound
Firstly this task requires running bloodhound on your VM however I had a lot of issues trying to get it to work. I don’t think it’s worth the effort and you’ll notice that the terminal I use changes before we run bloodhound, that’s me switching over to the TryHackMe Attack Box VM. Read over the information provided in the task and we’ll get started with the tasks.
SharpHound
Firstly from our CMD we’ll move over the SharpHound executable from the C:\Tools directory to our users Documents folder.
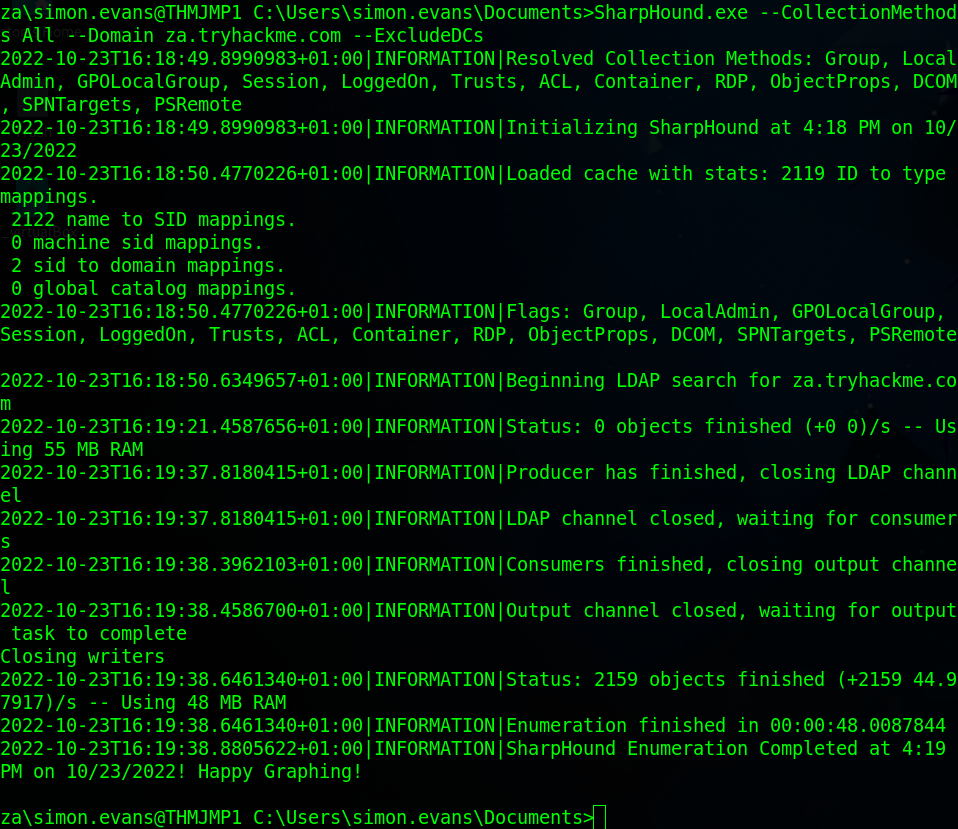
Now we need to run the command and get the answer to the first question. We are going to run SharpHound using the command “Sharphound.exe –CollectionMethods Session –Domain za.tryhackme.com –ExcludeDCs”, The collection method “Session” just does user session collection, this is a stealthy method of collection and only touches systems that are most likely to have user session data. Then the domain is specified which in this case is “za.tryhackme.com”, finally, the “–ExcludeDCs” instructs SharpHound not to touch the Domain Controller.
Once we’ve ran SharpHound we’ll need to move the data that SharpHound has generated over to the attack box. Use the secure copy command “scp simon.evans@THMJMP1.za.tryhackme.com:C:/Users/simon.evans/Documents/20221112191320_BloodHound.zip .”. The syntax for secure copy in this case was “scp <username>@<host>:<full file path> <output path>”.
Next to start BloodHound on the attack box we need to firstly run “neo4j console start” which will start the neo4j backend, a graphing data platform, basically database management. Once that’s started run “bloodhound –no-sandbox” in another instance to start BloodHound.
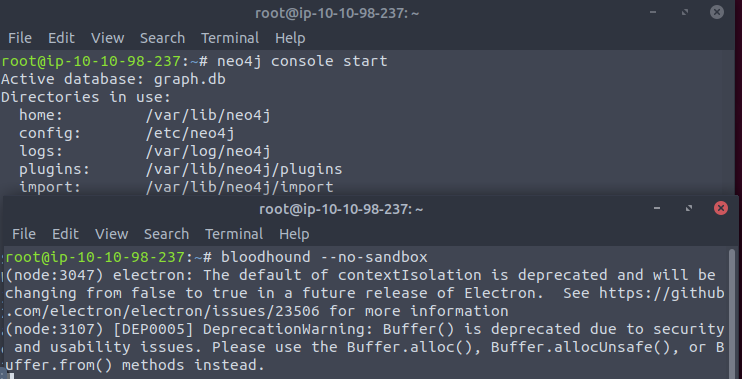
BloodHound is a really simple tool, once loaded drag and drop the SharpHound zip file onto the BloodHound window.
Once things have all loaded in have a play around with the interface and following the steps on the page you can make your way to this screen where you’ll be able to begin the next task.
From there open up the analysis tab and click on “List all Kerberoastable Accounts” to see all the accounts that are potentially kerberoastable, excluding the “krbtgt” account there are four others.
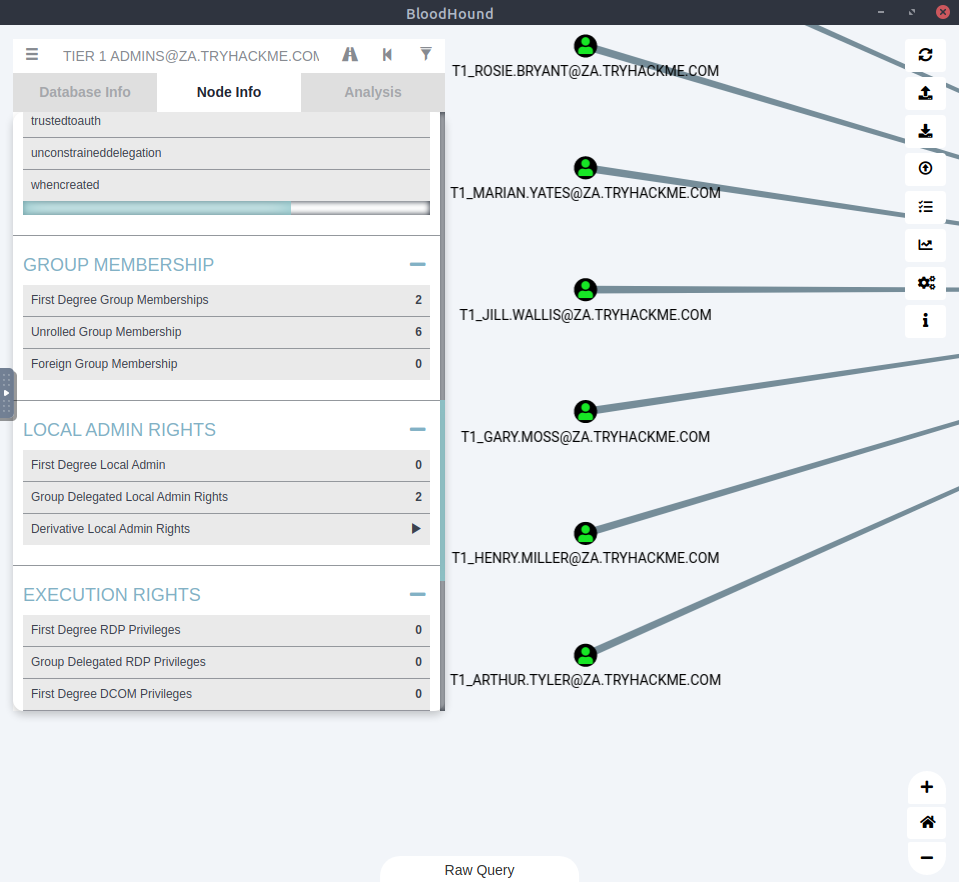
Next we’ll take a look at the “Tier 1 Admin” group display and try to find out how many machines this group have administrative access to.
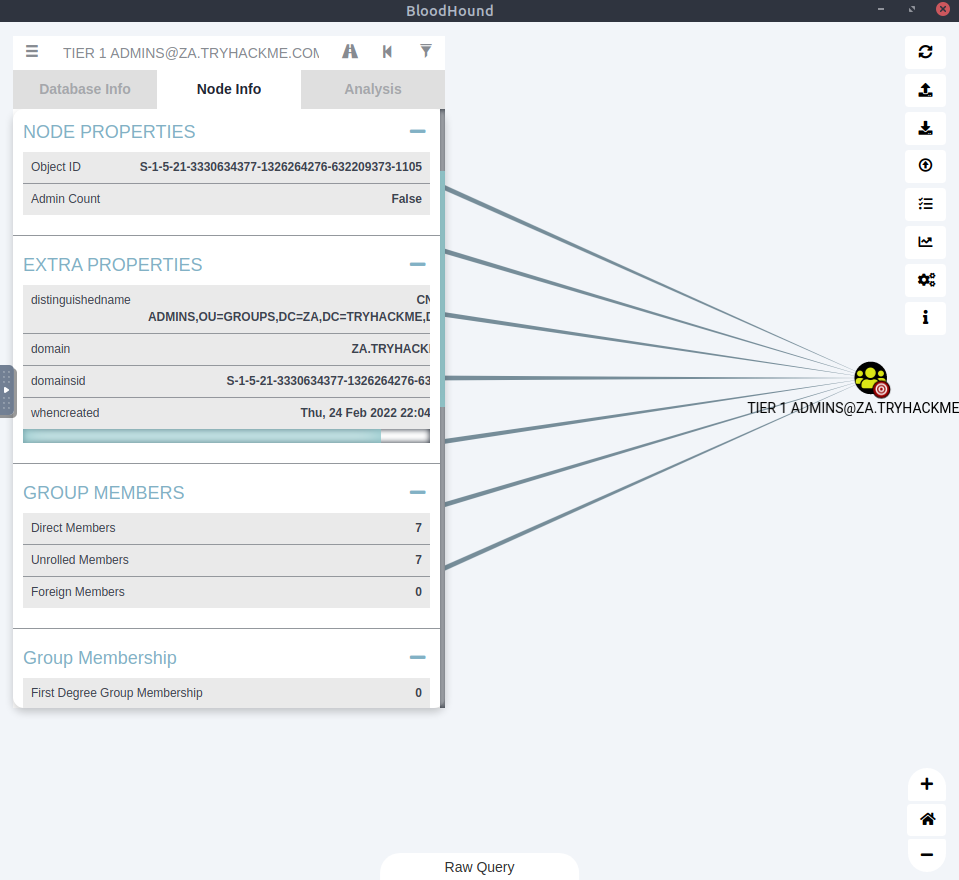
After scrolling we can see that the “Group Delegated Local Admin Rights” has a value of 2. This is a reference to the 2 machines that the admins can access.
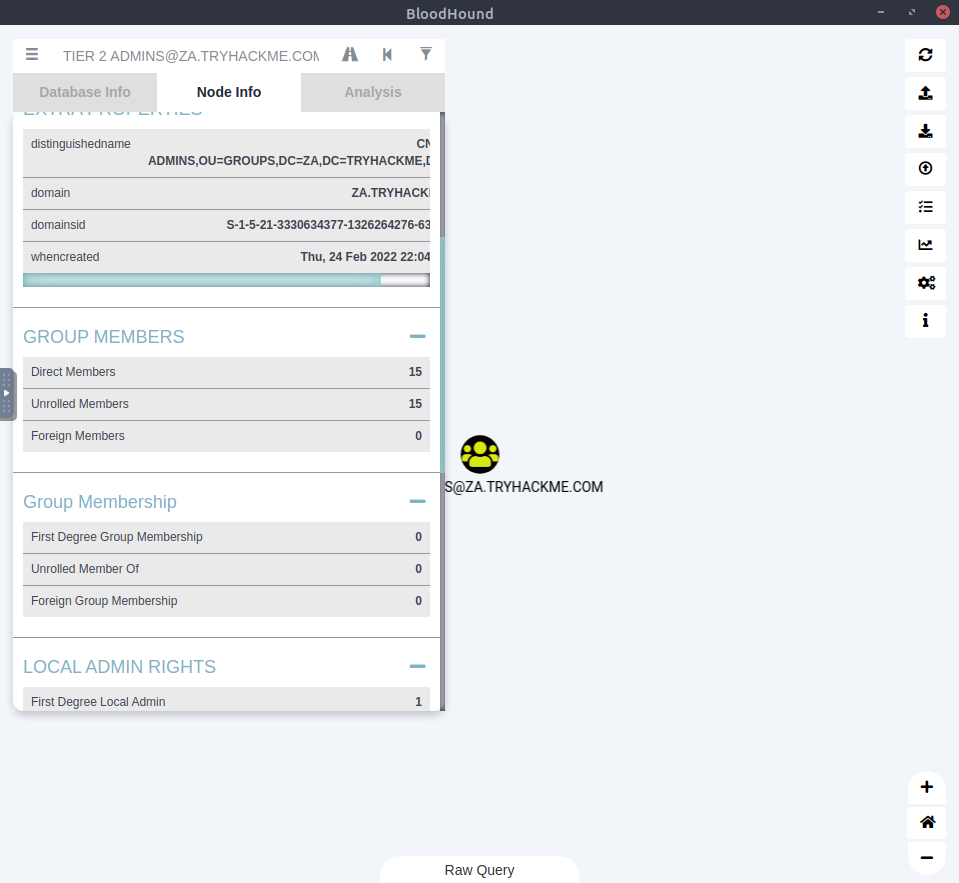
Lastly we’ll find all the members of the Tier 2 Admins group. Search for the group and click on the “Note Info” tab and we can see that there are 15 direct members of the Tier 2 admins group.
We can now finally answer the questions
What command can be used to execute Sharphound.exe and request that it recovers Session information only from the za.tryhackme.com domain without touching domain controllers?
Sharphound.exe –CollectionMethods Session –Domain za.tryhackme.com –ExcludeDCsApart from the krbtgt account, how many other accounts are potentially kerberoastable?
4How many machines do members of the Tier 1 Admins group have administrative access to?
2How many users are members of the Tier 2 Admins group?
15Task 7 – Conclusion
The conclusion has some interesting comments on other methods however I’d recommend looking at Power View or AD Explorer. Unfortunately we don’t get the Armatage style cracked boxes on the screen at the top however this was a job well done.


Thank you for being of assistance to me. I really loved this article.